tldr; I found this command injection vulnerability and registered it as CVE-2023-33617
This CVE is an Authenticated
Command Injection vulnerability. It affects Parks Fiberlink 210 routers, in the
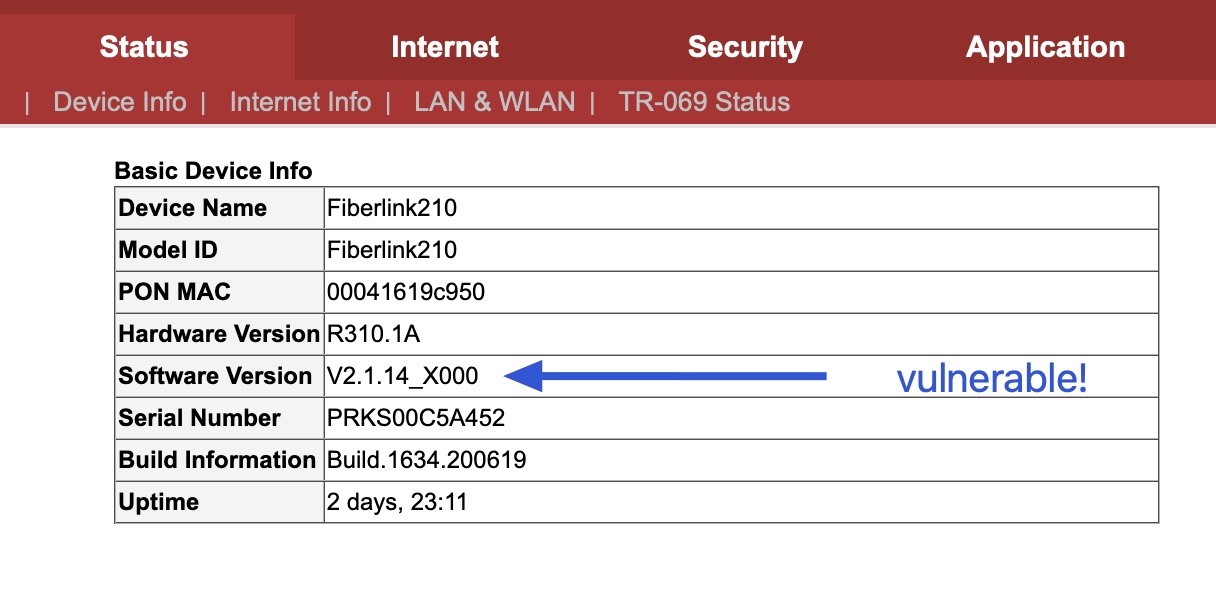
firmware version V2.1.14_X000.
This vulnerability has already been fixed in the version V2.1.15_X000, but
there are several vulnerable routers on the Internet.
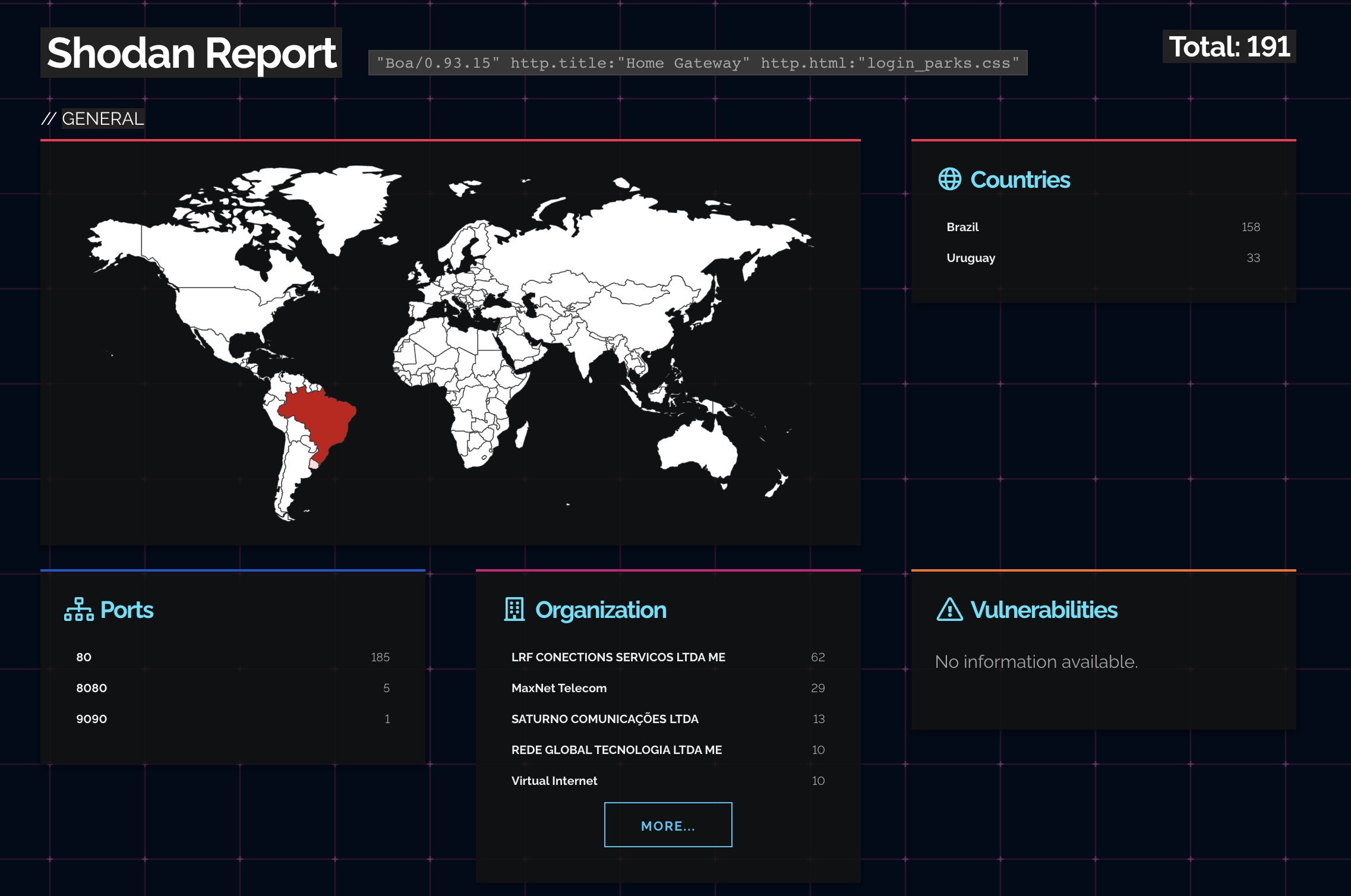
Parks is a Brazillian company that sells devices for enterprise, they seem to be the only ones who sell this router.
I’ve written an exploit in Python, here it
is. It
leverages the default credentials, which are admin:parks, and checks if the
version is vulnerable.
If you have access to a router and want to manually check if you’re vulnerable, check the “Software Version”.
Hacking IoT devices is fun
If you were here only for the technical details, that was it. Here I’ll write like I usually do in my other blogs and explain the story of how I found this vulnerabiliy.
Desktops nowdays have had their security significantly improved over the years, to the point that the Anti Virus that comes out of the box in Windows is not even bad. But have you ever heard about a router running an Antivirus? Have you ever seem a router be updated? Yeah, and guess what, routers are in a very good position in a network, they’re taken for granted and often have their security overlooked.
The thing that happens in routers that makes them specially vulnerable is that:
- They usually have a WAN and LAN interface.
- Vendors often use the same admin credentials for all the devices they ship.
- Exposing your router’s admin page to the Internet is as easy as changing the
listening interface from
127.0.0.1to0.0.0.0.
Once you have access to one of those devices, there are multiple ways to go from admin to root. Routers are a good target for exploitation so there are many public CVEs. But if you don’t find any exploitable CVE, there are two ways to go from there:
- Reversing firmware patches from the router itself and it’s software dependencies. (This is how we look for non-public vulnerabilities)
- Looking for 0-days.
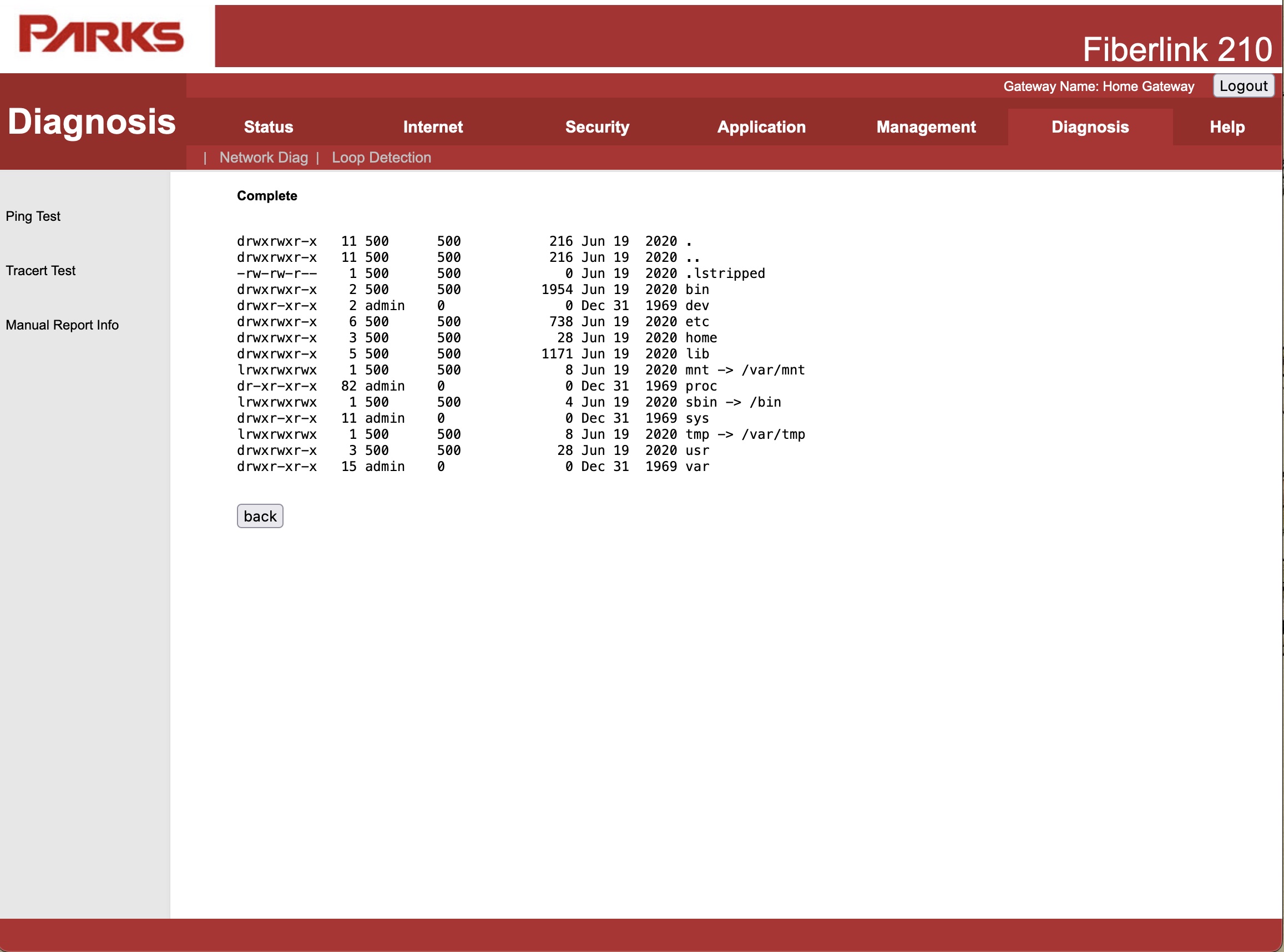
The approach that I like to use to find new vulnerabilities is to look for critical functionalities or dangerous funcionalities. e.g. The vulnerability for this CVE comes from the ping funcionality in the router, it takes user input and sends it to the ping command, this smells of command injection, and this is what I follow, the smell.
That’s it, Happy Hacking!